Funny how sometimes you don’t realize stuff until you actually try to interact with it instead of just observing it. I’ve used tcpdump many times behind a normal iptables ruleset, I’ve also used ‘dhclient eth0’ a lot of times. None of those times though did I realize that dhclient uses raw sockets and that iptables is unable to block those connections. As far as I can tell and with some help from the #netfilter guys on freenode it seems you can’t block raw socket connections at the moment in an easy way. It’s not as bad as it sounds though since you either need root privileges or the CAP_NET_RAW capability to be able to use raw sockets.
If you want to see this for yourself do the following:
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT DROP
Now try to resolve something or connect to something:
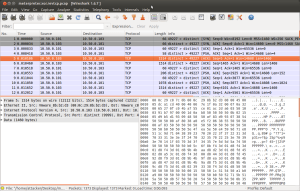
DNS resolving
host http://www.google.com
;; connection timed out; no servers could be reached
TCP connect
nc -vv 173.194.112.51 80
nc: connect to 173.194.112.51 port 80 (tcp) failed: Connection timed out
Now if you do this with raw sockets, using scapy for example:
DNS resolving
>>> a,u = sr(IP(dst=”208.67.220.220″)/UDP(dport=53)/DNS(rd=1,qd=DNSQR(qname=”www.google.com”)))
Begin emission:
Finished to send 1 packets.
*
Received 1 packets, got 1 answers, remaining 0 packets
>>> print a.show()
0000 IP / UDP / DNS Qry “www.google.com” ==> IP / UDP / DNS Ans “173.194.112.51”TCP connect
>>> a,u = sr(IP(dst=”173.194.112.51″)/TCP(sport=3445))
Begin emission:
Finished to send 1 packets.
*
Received 1 packets, got 1 answers, remaining 0 packets
>>> print a.show()
0000 IP / TCP 10.50.0.103:3445 > 173.194.112.51:http S ==> IP / TCP 173.194.112.51:http > 10.50.0.103:3445 SA / Padding
Like you can see the resolving works fine and the TCP connection attempt also works fine since we receive a SYN+ACK, this is all happing while we have our iptables policy on DROP. Fun stuff right?
In my opinion this doesn’t really have a lot of real world usage, even though some backdoors as referenced before in my post about connectionless backdoors use the raw socket sniffing method to activate themselves. It could come in handy though if you become root on a server with a strict firewall and you don’t want to alter the firewall, you could use raw sockets for sending and receiving to cut right through it.
If you are wondering QP stands for Quick Post.